Mobile ID AZ Simplified

The concept of Mobile ID, also known as Mobile Identity, has been gaining traction in recent years, especially with the rise of digital transactions and online services. In this context, Mobile ID AZ refers to the specific implementation of Mobile ID technology in Azerbaijan, aiming to provide a secure, convenient, and unified digital identity solution for citizens. To understand the significance and functionality of Mobile ID AZ, it's essential to delve into the broader context of digital identity, its challenges, and how Mobile ID technology addresses these challenges.
Introduction to Mobile ID Technology
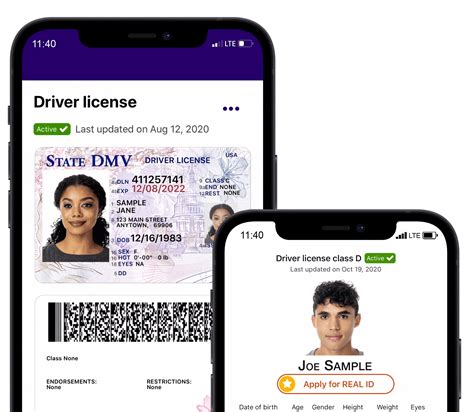
Mobile ID technology utilizes a mobile device, such as a smartphone, as a primary means of authentication and identification. It combines the uniqueness of a mobile number with advanced security features, such as biometric data (e.g., fingerprints, facial recognition) and encryption, to create a robust digital identity solution. This technology has the potential to replace traditional physical identification documents, such as passports and driver’s licenses, for various digital transactions and services.
Benefits of Mobile ID
The implementation of Mobile ID offers several benefits, including enhanced security, convenience, and efficiency. By leveraging biometric data and secure encryption, Mobile ID significantly reduces the risk of identity theft and unauthorized access to personal information. Additionally, it provides users with a convenient and easy-to-use method for authentication, eliminating the need to carry physical identification documents. From a broader perspective, Mobile ID can facilitate the development of digital economies by providing a trusted and unified digital identity framework.
| Feature | Description |
|---|---|
| Security | Utilizes biometric data and encryption for secure authentication |
| Convenience | Eliminates the need for physical identification documents |
| Efficiency | Streamlines digital transactions and services |

Key Points

Key Points
- Mobile ID AZ aims to provide a secure and convenient digital identity solution for citizens.
- The technology leverages biometric data and encryption for authentication.
- It offers benefits such as enhanced security, convenience, and efficiency in digital transactions.
- The success of Mobile ID AZ depends on striking a balance between security and user convenience.
- Implementation challenges include ensuring widespread adoption, addressing privacy concerns, and maintaining high security standards.
Challenges and Future Directions
Despite the potential benefits, the implementation of Mobile ID AZ faces several challenges, including ensuring widespread adoption, addressing privacy concerns, and maintaining high security standards. To overcome these challenges, it’s crucial to engage in public awareness campaigns, collaborate with stakeholders to address privacy and security concerns, and invest in continuous technology updates to stay ahead of emerging cyber threats.
The future of Mobile ID AZ and similar technologies around the world will be shaped by how effectively these challenges are addressed. As digital transactions continue to grow, the demand for secure, convenient, and unified digital identity solutions will increase. Mobile ID technology, with its potential to provide a seamless and secure authentication process, is well-positioned to meet this demand, provided that the necessary investments in security, privacy, and user experience are made.
What is Mobile ID AZ, and how does it work?
+Mobile ID AZ is a digital identity solution that uses a mobile device for authentication, combining a mobile number with biometric data and encryption for secure identification.
What are the primary benefits of using Mobile ID AZ?
+The primary benefits include enhanced security, convenience, and efficiency in digital transactions, as well as the potential to replace traditional physical identification documents.
How secure is Mobile ID AZ against cyber threats?
+Mobile ID AZ utilizes advanced security features such as biometric data and encryption to protect against cyber threats. However, the security of the system also depends on continuous updates and investments in security measures.



